🏗️ Reference Architecture
Lumos Enterprise Architecture and Deployment Strategy
1. Introduction
Lumos is the first Autonomous Identity Platform that automatically discovers and manages access across all your apps. It goes beyond traditional IGA by delivering:
- 🔎 Complete Visibility: Uncover every app, identity and permission to see your entire access landscape.
- 💡 Actionable Insights: Lumos pinpoints the biggest security risks and costs inefficiencies, giving teams clear direction to reduce access sprawl effectively.
- ⚙️ Full Automation: Automate the whole identity lifecycle from joiner-mover-leaver workflows to JIT access to access reviews.
- 🔄 Adaptive Systems: Keep RBAC policies up-to-date with AI as your organization evolves.
As organizations look to modernize their identity infrastructure, Lumos can be introduced in two distinct ways:
- ⚖️ Co-existence Model: Lumos coexists with existing Identity Providers (IdP) or IGA platforms—Okta, Microsoft Entra ID, SailPoint, Saviynt, or even manual processes—initially focusing on enhancing capabilities such as Access Visibility, Access Reviews, and Self-Service provisioning. Over time, Lumos can “strangle” or replace legacy functionality if desired.
- 🧭 Direct Lifecycle Model: Lumos serves as the central identity lifecycle management platform, connecting directly to HRIS and orchestrating the creation and deactivation of core accounts (e.g., in AD, Okta, and beyond).
Patterns of Legacy Displacement describes how organizations can continue to deliver business needs while at the same time replace outdated technology through:
- Understanding the outcomes you want to achieve
- Deciding how to break the problem up into smaller parts
- Successfully delivering the parts
- Changing the organization to allow this to happen on an ongoing basis
This document covers the architecture for both approaches the co-exist and direct models, the pros and cons of each, and when each may be most appropriate.
2. Architectural Overview
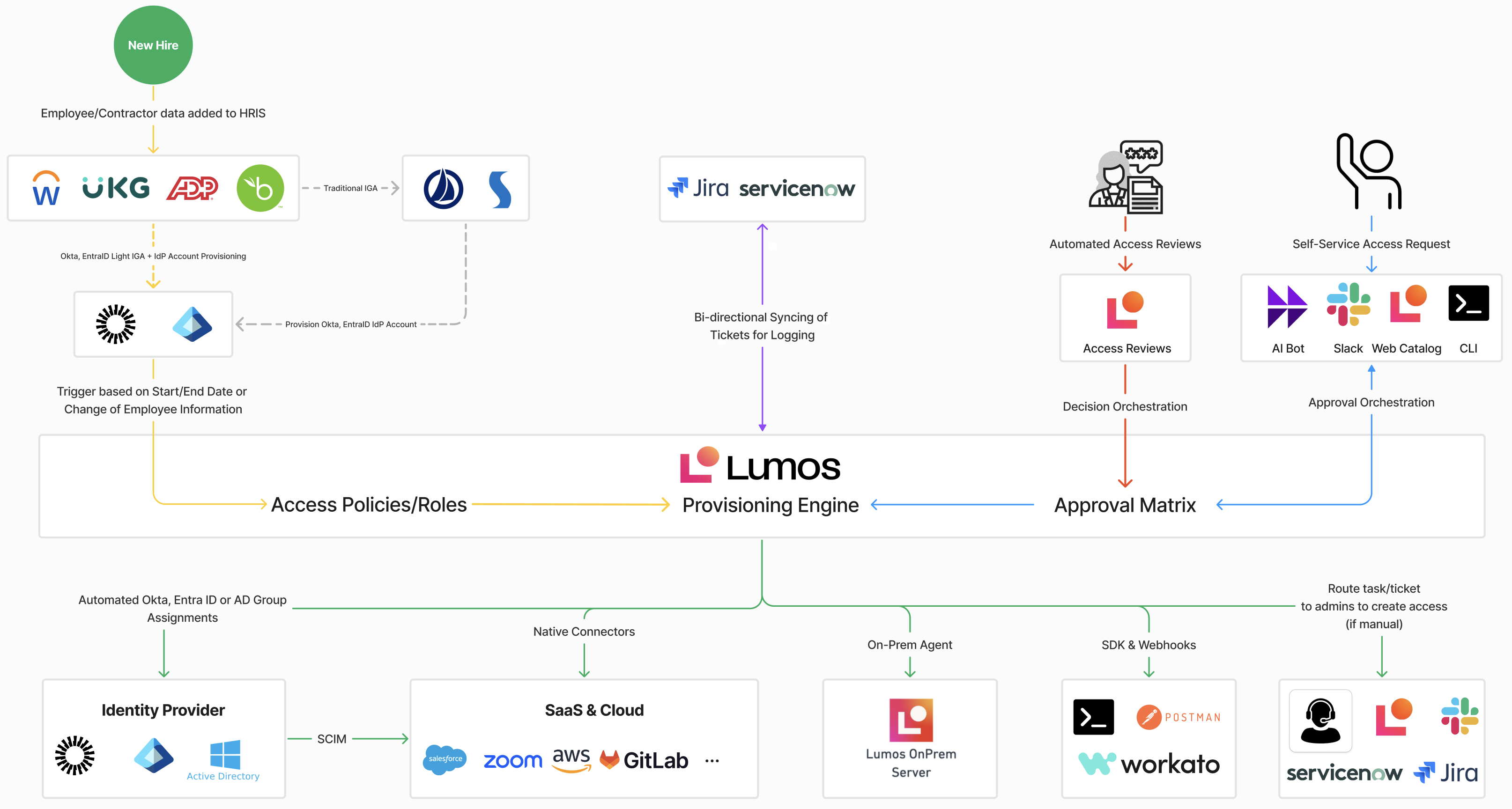
Below is a high-level architecture diagram illustrating Lumos’ components and integrations.
Key Components
- HRIS: Often the “source of truth” for employee data, including start/end dates, job function, department, etc. Examples: Workday, PeopleSoft, UltiPro.
- Identity Provider / Directory: Manages core employee accounts (e.g., email address, corporate login credentials). Examples: Microsoft Entra ID, Okta, Active Directory.
- Lumos Provisioning Engine: Central orchestration layer for all access and permission events. Enforces Joiner-Mover-Leaver rules based on HRIS or IdP data. Leverages an Approval Matrix to automate or route access requests for manager or security approval.
- Self-Service Access Request Layer: Multiple user-facing “front ends” for access requests (AI Bot, Slack, Web Catalog, CLI). Integrates with the Provisioning Engine to request permissions, roles, or group membership.
- Automated Access Reviews: Compliance and security access reviews. Integrates with Lumos Provisioning Engine for closed-loop remediation.
- SaaS & Cloud Connectors: Native connectors (SCIM, proprietary APIs) to systems like Salesforce, Zoom, AWS, GitLab, etc.
- On-Premise Agent: Optionally deployable inside a customer’s on-premise environment to manage legacy or custom apps.
- ITSM Integrations: Bi-directional ticket syncing for logging, approvals, or additional workflows if needed. Examples: Jira, ServiceNow.
3. Deployment Model 1:
⚖️ Co-Existence with Existing IdP / IGA for Lifecycle Management
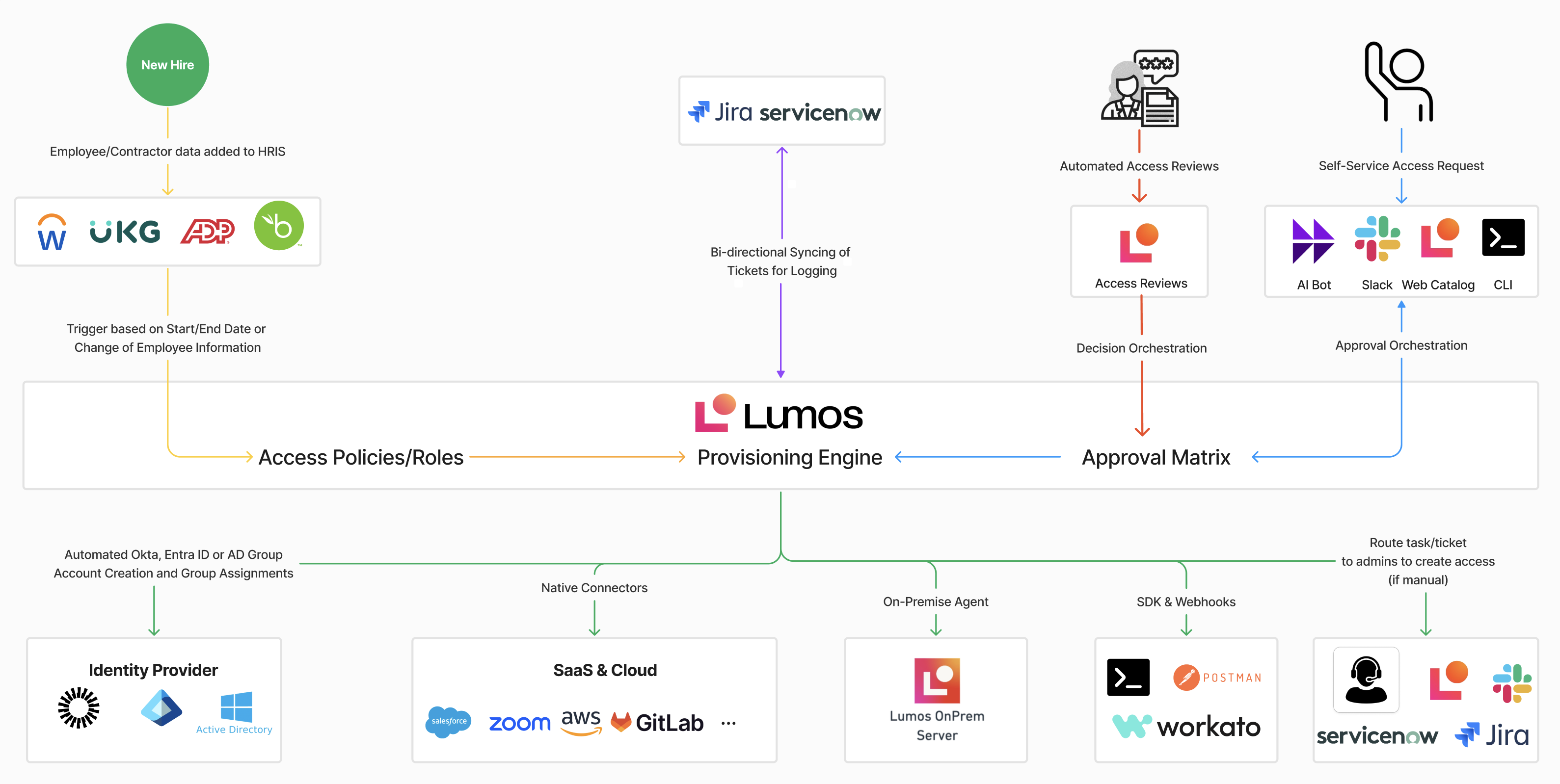
3.1 Overview
In this model, Lumos relies on the organization’s existing IdP (e.g., Okta, Entra ID) or even a legacy IGA platform (e.g., SailPoint, Saviynt) for core identity creation. The HRIS triggers new user creation in the existing IdP. Lumos then ingests user attributes, group memberships, or job changes from the IdP to drive advanced governance functionality including:
- Access Reviews: Streamline user access reviews with a better user experience and more automation.
- JIT AppStore: Fine-grained, time-based provisioning into AWS, GCP, and more to achieve true least-privilege access.
- SaaS Management: Eliminate license waste and prevent true-ups with usage analytics and automated reclamation of unused licenses.
- Policy Agents: Mining policies is only the first step. Agents take it further by automating ongoing enforcement and updates.
Key Points
- Source of Identity: HRIS → Existing IGA/IdP → Lumos
- Access Requests and Access Reviews: Handled through Lumos (AI Bot, Slack, Web Catalog, CLI)
- Provisioning & Approvals: Lumos automates permissions, roles, and group membership. If the IdP or IGA tool already has partial provisioning in place, Lumos can add advanced layers (e.g., Access Reviews, “AppStore” requests).
- Joiner-Mover-Leaver: The existing IdP or IGA performs the initial account creation; Lumos handles deeper or more granular provisioning steps for specific SaaS/Cloud apps.
3.2 Pros and Cons
Pros
- Faster Time to Value: Minimal disruption to existing processes. Lumos can be overlaid for Access Reviews, advanced request flows, and visibility without a full rip-and-replace.
- Reduced Risk: Existing user creation paths remain intact; major changes in the short term are not required.
- Incremental Adoption: Start with key pain points (e.g., Access Reviews, “Shadow IT” app provisioning) and expand over time.
Cons
- Partial Lifecycle Control: Account provisioning/deprovisioning is still managed in multiple places.
- Complexity: Maintaining data synchronization between multiple identity systems.
3.3 When to Choose Co-Existence
- You have significant investment in an existing IdP or legacy IGA platform.
- You need a quick win with Access Visibility, Reviews, or a user-friendly Access Catalog (AppStore).
- You want to minimize disruption while modernizing identity and access governance.
4. Deployment Model 2:
🧭 Direct Lifecycle Management with Lumos
4.1 Overview
In the Direct Lifecycle model, Lumos ties directly to the HRIS (e.g., Workday) for new hires, terminations, or changes. Lumos becomes the “system of record” for identity events and orchestrates the creation or modification of identities across directories (e.g., Entra ID, Okta) and other downstream systems.
Key Points
-
Source of Identity: HRIS → Lumos → IdP(s)
-
Account Lifecycle:
- Joiner: Lumos automatically creates accounts in the directory (Entra ID, Okta, AD) and in relevant SaaS apps.
- Mover: A change in Workday triggers appropriate role/group changes.
- Leaver: Automatically disables and/or removes access on the user’s last day.
-
Full Provisioning Control: Lumos uses native connectors (SCIM, APIs) or an on-prem agent to orchestrate provisioning across all systems.
4.2 Pros and Cons
Pros
- Unified Lifecycle Management: Lumos has end-to-end visibility and control over identity events, ensuring consistent user provisioning.
- Improved Automation: No need for duplicate logic in multiple tools—simplifies the overall architecture.
- Future-Proof: As new apps or directories are introduced, Lumos remains the single orchestration layer.
Cons
- Bigger Organizational Shift: Requires buy-in to rely on Lumos as the single authoritative provisioning system.
- Migration Overhead: Potentially migrating existing logic from the legacy IdP or IGA into Lumos.
- Longer Time to Value: More up-front planning and integration steps.
4.3 When to Choose Direct Lifecycle
- You do not already have or plan to phase out an existing IGA tool.
- You want end-to-end identity lifecycle automation from the start.
- You have a relatively greenfield environment or want to invest in a more modern approach.
- You prefer having Lumos as the single orchestration across multiple IdPs and cloud/on-prem targets.
5. Recommended Adoption Strategy
Many organizations choose a phased approach:
- Phase 1: Co-exist with existing IdP / IGA. Implement Lumos for Access Requests, Approvals, and Access Reviews.
- Phase 2: Migrate more joiner-mover-leaver logic into Lumos as you gain comfort with the platform.
- Phase 3: Decommission or reduce reliance on the legacy IGA or redundant provisioning tools, allowing Lumos to serve as the unified lifecycle management engine.
By starting with Lumos’ self-service AppStore and Access Reviews, you gain fast value—improving user experience and compliance—without fully re-architecting identity management. Over time, you can leverage Lumos for full lifecycle automation if/when the business requires it.
6. Conclusion
Lumos is designed to meet customers wherever they are on their identity governance journey—whether that means layering on top of existing identity providers or becoming the core lifecycle management platform. With its modern UI, flexible connectors, and powerful rules engine, Lumos simplifies and modernizes both daily access operations and long-term governance workflows.
In Summary:
- Co-Existence Model is typically faster to roll out, less risky, and ideal if you already have a strong IdP or partial IGA tool in place.
- Direct Lifecycle Model provides a single, powerful orchestration engine and is the best path if you want to converge your identity and access management under one platform—or don’t already have a robust system in place.
Regardless of which model you adopt first, Lumos’ modular architecture and broad integration capabilities ensure you can evolve toward a fully modern, automated identity governance posture with minimal friction.
Updated 10 months ago